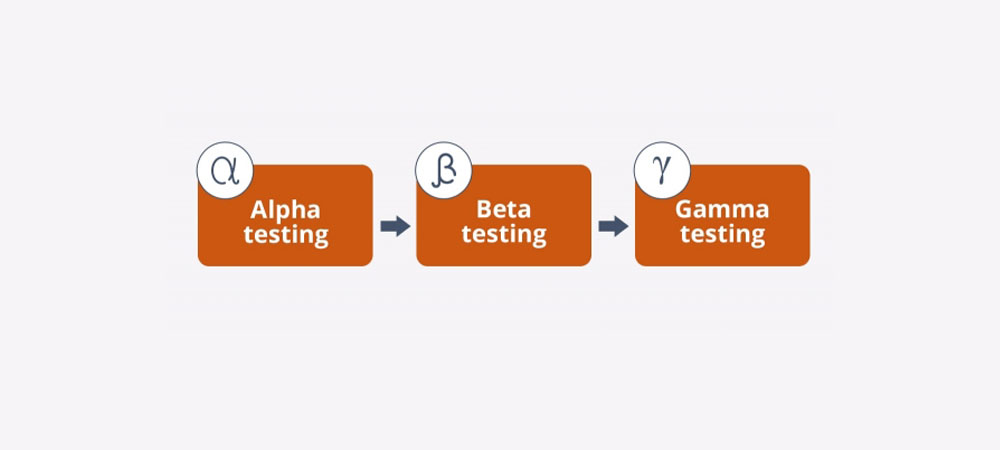
The advancements in Agile and DevOps processes have led to changes in the way a software application is written, tested…
Ray Parker
Modern-day defect tracking software provides ease of use for testers and developers but they can still give a tough time…
Testing, as we all know, is an important part of the post-development stage to ensure that the application works as…
Penetration testing is a technique where authorized/ethical hackers simulate an attack on specific applications, networks or websites to assess their…
According to a report by the Systems Sciences Institute at IBM, ‘the cost to fix an error found after product…
2020 is expected to be an impactful year for the cyber security of all businesses. If we look back at…
There is a lot of competition in all the sectors and fields of the world. Whether one goes for a…
The digital revolution is not limited to upgrading security mechanisms or introducing alternatives in different disciplines. It also relates to…
A blockchain is an expanding list of records called blocks, which are connected using cryptography. Blockchains which are readable by…